Presenter: Megumi Niki
Date: June 23rd, 2022
Part presented: Chapter 5. Building trust for data-driven innovation
Presentation summary
According to the book, two main components of trust for data-driven innovation are security and privacy protection. On the topic of security, the authors compare the traditional and the current and recommended approaches to achieving security. On the topic of privacy protection, the authors discuss the privacy-related impact of data-driven innovation, practical means to prevent information discovery, and policy approaches to protect privacy. In this report, I will share the security portion of the presentation.
Security
The digital assets of individuals, governments, and businesses face intentional and unintentional threats from organized crime groups, foreign governments, hackers, hardware failure, natural disasters, and more. These threats can cause damages to the functions of systems and networks, which can then cause damages to the social and economic activities that rely on the availability, integrity, and confidentiality of data and information.
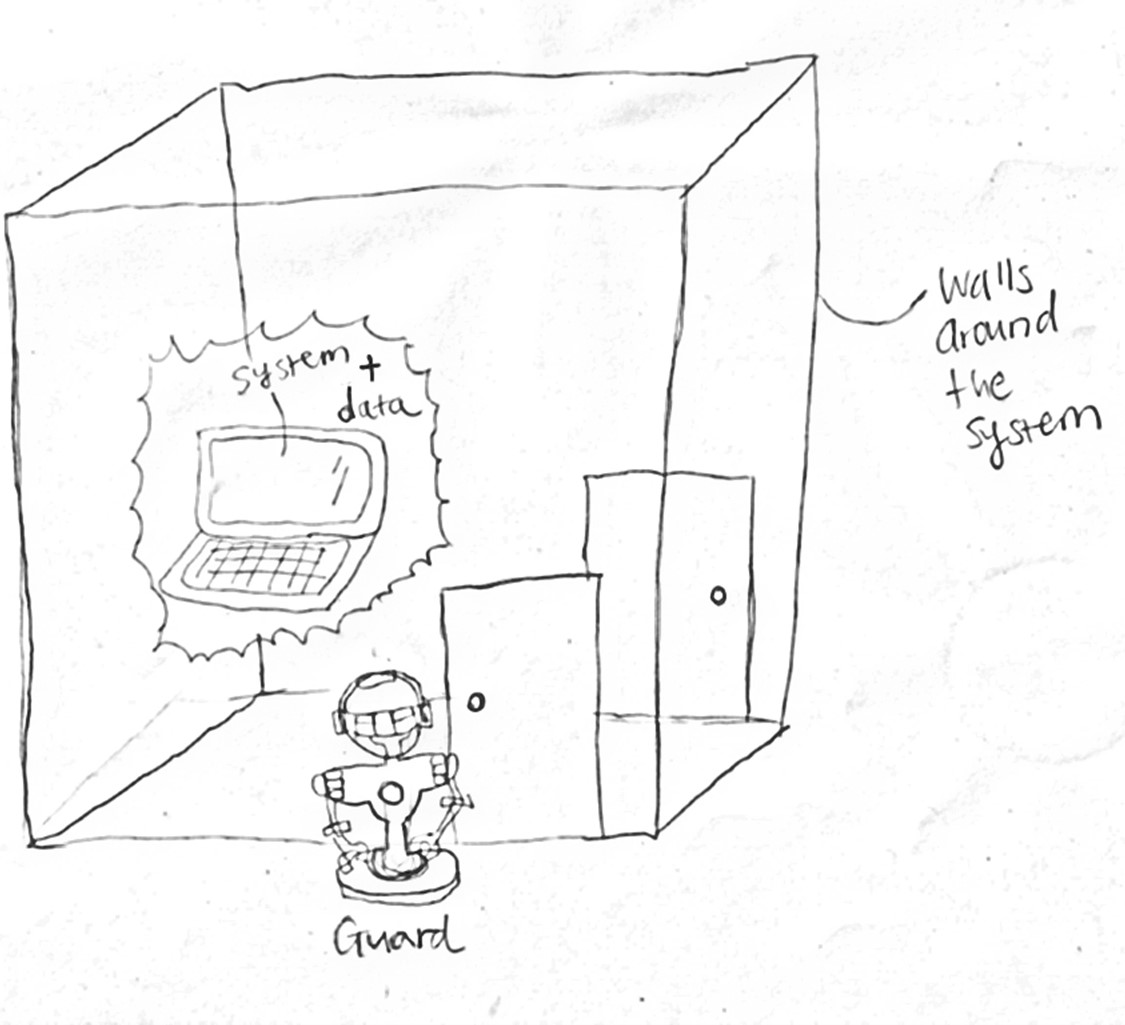
In the traditional approach, security is defined as “free from danger or risk of loss.” An organization would set in security measures, and at this point the system and data are deemed protected. The system and data are locked inside a metaphorical security room, as depicted in Figure 1, and in order to strengthen security, the walls are heightened, doors are controlled, and guards are added. The IT department of the organization is often in charge of all thing’s security.
Figure 1. Traditional approach to security
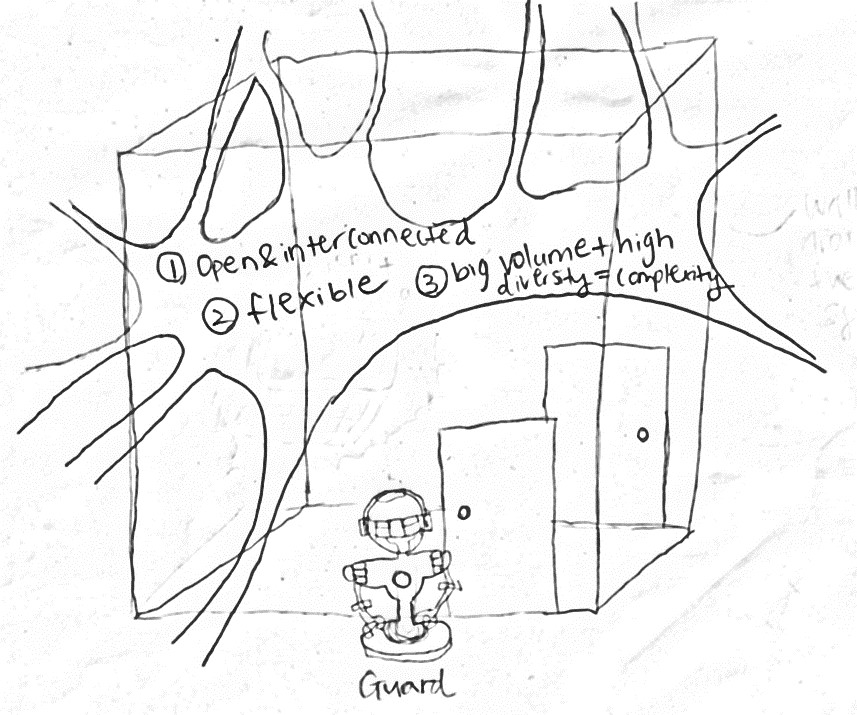
However, the systems, data, and networks needed for data-driven innovation are open, interconnected, flexible, voluminous, diverse, and complex, which means they cannot be contained within walls, as illustrated in Figure 2.
Figure 2. Limitations of the traditional approach to security
Therefore, the authors call for a shift from “security” to “risk management” as a core philosophy. Risk management is defined as an activity to “increase the likelihood of economic and social benefits from the data volume cycle by minimizing potential adverse effects of uncertainty related to the availability, integrity, and confidentiality of the cycle.” Risk elimination is impossible, and an organization must find the right balance between risks and benefits. This means that owners of benefits should also be owners of risks and that effective communication between and among business and IT actors is necessary.
Discussion summary
Below I will summarize some of the opinions shared in our discussion.
- With the rise of AI use, discrimination is a stronger concern now. Algorithms can be racist, sexist, and otherwise discriminatory because they are often trained using data that already contain different biases and prejudices. It is crucial that developers are always aware of this problem and that they actively try to remove the biases.
- Some friends actually deleted Facebook and other social media accounts following data leak issues. Therefore, it is possible that some people would make conscious and active decisions regarding service use on the basis of privacy protection. However, not everyone has the resources or the ability to collect information on how each service is working to ensure privacy protection and to withdraw from using certain services that are sometimes engrained in our lives as digital infrastructure. It is important that governments intervene effectively and strictly.
- When you finish all of your job-hunting processes in Japan, it is very difficult to have all of your information deleted. Some companies and websites let you delete your account completely, while others don’t. Sometimes a website does not have an unsubscribe button and you need to make a phone call to ask to have your information removed.
- In Japan, it is more difficult to unsubscribe from mailing lists than in the U.S. where it is required by law that a consumer can unsubscribe with just one click.
- The use of surveillance cameras and facial recognition technologies should be limited to some extent. It would be uncomfortable and scary to have so many cameras everywhere observing every single thing you do.